Mantap
Utuh Wibowo
Explore The Magnificent Of Cyberworld
Hello, welcome to my private website. Hope you will enjoy visiting this website, find nice things about me and also get some information that you may interested. I just share a little part about the path that I choose in my life journey and adventures.
- NameUtuh Wibowo
- BornProbolinggo
- StatusMarried
- HobbyModification
- ReligionIslam
- PoliticalIndependent
- CountryIndonesia
- Emailutuh@outlook.com
Probolinggo - Jakarta

Password to Download:
FREEFORALL
Utuh Wibowo
My Profile

- NameUtuh Wibowo
- AddressProbolinggo - Jakarta
- GenderMale
- ReligionIslam
- NationalityIndonesia
- PoliticalIndependent
- E-mailutuh@outlook.com
Best Practice
Information Technology
- COBIT
- ITIL
- PBI
- CMMI
- PMP
Information Security
- ISSAF
- CISA
- CISSP
- CGEIT
- ISO 27001
- ISO 27002
- NIST
- CSC
- PCI DSS
Project Management
- Agile
- Scrum
- Classic
Personal Skills
- Leadership
- Management
- Coaching
- Strategic
- Communication
- Negotiation
- Relationship
- Presentation
General Skills
- Consultation
- Audit
- Project Cycle
- System Integration
- Risk Management
- Security Policy
- Compliance
- Business Ideas
- Financial Banking
- Sales & Marketing
- Credit Processing
- Digitalization
- E-Commerce
- Resource Plan
- Time Management
- Office Automation
Technical Skills
Web Design
- HTML
- ASP
- CSS
- JSP
- PHP
Programming
- Java
- C/C++
- C#
- VB.NET
Database
- Oracle
- MySQL
- SQL Lite
- MS SQL
Networking
- TCP/IP v4/v6
- Subnet v4/v6
- Firewall
- DNS/DHCP
- Active Directory
Operating Systems
- Windows
- Sunsolaris
- Linux
- Mac OS
- FreeBSD
Internet Of Things
- Big Data
- Cloud Computing
- Intelligence
Prologue
Hello there, let me introduce my self.
Leading a company is enjoyable for me. I'm honest, energetic, simple, flexible, hardworking, comprehensive, easy going, curious with unexpected ideas, adapt with new environment quickly, enjoy to learn something especially about technology, self-motivated person, able to meet objective and complete any challenges as a champion.
More than 14+ years extensive work experience in the area of business and systems planning, analysis, networking, infrastructure, security, programming, development, testing and management for some top company. Good relationship with many reputable IT vendors. Excellent interpersonal, communication, presentation and negotiation skills. Having strong leadership with ability to manage a group of people.
Careers
2023 - Now
Universal Consultancy Indonesia
Chief Artificial Intelligence
2008 - 2023
Indojasa Technology Solution
Executive Chairman
Independent Advisor
2004 - Now
Independent Consultant
Information Technology Consultation
Information and Technology Audit
Digital Enterprise Development
Critical Technology Transformation
Big Data Analytics and Cloud Computing
Enterprise Technology Solution
Program and Project Management
Risk Assessment and Mitigation
Data Center and Data Warehouse
Database Tuning and Optimization
Policy, Procedure and Compliance
Business and Systems Analyst
Web Design and Development
Content Management Systems
Research and Development
Disaster Recovery Management
Master Data Management
Customer Relationship Management
Strategic and Tactical Road map
Enterprise Resource and Human Capital
Business Intelligence Technologies
Search Engine Optimization
Intrusion and Prevention Detection System
Mobile Technology Solution
Data Architecture and Modelling
Performance Acceleration System
Maintenance and Help desk Support
Customer Experience and Engagement
Sales and Marketing Application
Online Shop and E-commerce Solution
Services and Contact Center
Digital Media and Marketing
Product Quality Assurance
Internet of Things
Private Consultant
Information Security Best Practice
Cyber Security and Digital Investigator
Security Attack and Penetration Testing
Troubleshoot and Patching
Social and Reverse Engineering
Malware and Antivirus
Cyber Criminals Hunter
Personal Activities
Serial Businessman
General Investor
Technology Researcher
Bug Bounty Hunter
Internet Freedom Fighter
Free Software Volunteer
Open Source Activist
Modificator Specialist
Public Speaker
Author and Chief Editor
2016 - 2018
Integra Media Dinamika
Chief Business and Operation Officer
2016 - 2018
CreateAppsHere
Managing Director - South East Asia
2014 - 2016
Infimedia Solusi Pratama
Chief Technology Officer - Project Director
2013 - 2014
Bank Danamon Indonesia Tbk
IT Senior Technology Project Manager
IT System Integration Manager
IT Auditor Team Leader
2011 - 2012
Sinergi Daya Mitra
Senior Project Manager
System Integration Manager
2009 - 2010
Ecomindo Sarana Cipta
Project Manager
Senior IT Auditor
2008 - 2008
Ganesha Consulting Group
Senior IT Auditor
Senior IT Consultant
2007 - 2007
Cybertech Solusindo
IT Security Manager
IT Development Specialist
2006 - 2006
Elektronik Lestari
IT Systems Engineer
IT Business Development
2004 - 2005
Resultan
IT Maintenance and Support
IT Network Systems Engineer
2001 - 2003
Freelancer
Web Developer
Systems Support
Programmer
Network Engineer
Operator Plus
List of my project on Linkedin: Latest Projects
If you interest to know more, feel free to contact me: contact@utuhwibowo.com
-
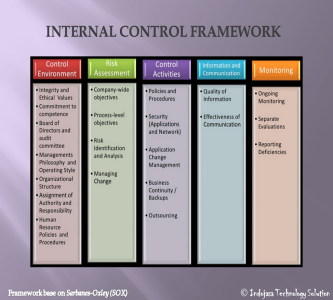
Objective of Internal Control
Client: Tech Company, Banking, Public and Private Company
• Compliance with applicable law and regulation.
• Achieve goals by provide authorization, completeness, accuracy, validity, physical safeguards and security, error handling and segregation of duties.
• Protect the assets of the business from misuse, theft, accident, fraud etc.
• Promotes operational effectiveness and efficiency.Thank you.. -
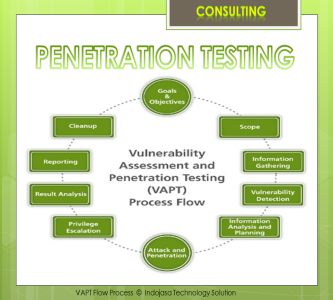
Objective of Penetration Testing
Client: All Sector
• Identifying and classification of the vulnerabilities.
• Helping organizations meet regulatory compliance.
• Providing evidence of real status of the systems.
• Providing a detailed report to the management.
• Find inadequate security control, configurations and policies.
• Know the level of security of an environment also to evaluate the response to an intrusion or to an incident.Thank you.. -
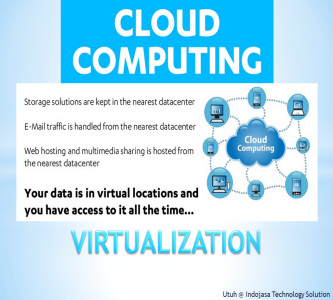
Objective of Cloud Computing
Client: Public and Tech Company
• Obtain access speed, deployment and performance.
• Gain the best redundancy and systems uptime.
• Data in virtual location and can be accessed anytime.
• On-demand scalability of highly available and reliable pooled computing resources.
• Automated disaster recovery and software updated.
• Reduce infrastructure total cost and easier collaboration.Thank you.. -
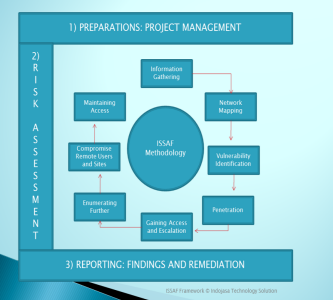
Objective of Implementing ISSAF
Client: All Sector
• Find and know the weakness and increase security systems.
• Reduce risk into an acceptable level and maintain on that level.
• Protects critical assets, people, process and infrastructure.
• Improve alignment with technology control.
• As a reference to improve standard operating procedure and guidelines.Thank you.. -
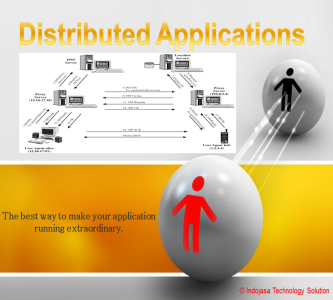
Objective of Distributed Application
Client: Banking, Public and Tech Company
• Increase scalability and stability of application.
• Provide better performance, availability and satisfaction for user experience.
• Produce good service and operational level agreement.
• High capability and redundancy of application.
• Reduce application and database systems load.
• Minimize impact of systems and network failure.Thank you.. -

Objective of Communication Management
Client: All Sector
• Active listening, providing positive reinforcement, questioning ideas to gain clarification.
• Negotiating, Conflict resolution, Persuasion.
• Provides critical links among people, ideas and information.
• Information is provided at right format, at right time, to right person with right impact.
• Creating, collecting, distributing, storing, and retrieving information.Thank you.. -

Objective of Enabling Process Quality
Client: Public and Private Company, Personally
• Provide quality plan, metric and checklist.
• Provide good interaction and communication with all parties.
• Improve work processes and efficiency development.
• Find and track problems then fix problem during process.
• Controlling process to meet with current standard, policies and compliance.
• Ensure outcome of product have the highest quality.Thank you.. -

Objective of Risk Management
Client: Public and Private Company, Government and Personal
• Proactive action rather than reactive approach.
• Reduces surprises and negative consequences.
• Provides better control over the future.
• Provide right decision for organization and better risk maintenance.
• Improves chances of reaching good performance.
• Improve efficiency, effectiveness and profit for organization.Thank you.. -

System Development Life Cycle
Client: All Sectors
• Deep knowledge of 4 phases SDLC: Planning, Analysis, Design, Implementation
• Flow process of Structured Design – formal step-by-step approach, Rapid Application Development – focuses on quick development, Agile - eliminates documentation overhead and modelling.
• Each phase is composed of steps that rely on techniques that produce deliverables.
• Developing good and satisfaction systems.Thank you.. -
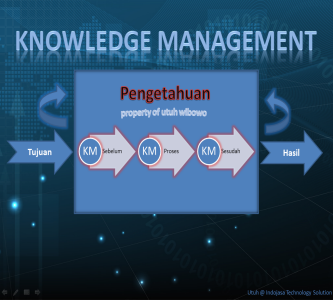
Objective of Knowledge Management
Client: Public Company
• Achieved target through creating, sharing and applying knowledge.
• Identifying, organizing, transferring and using the valuable information.
• Applying a systematic approach to the capture, structure, management and dissemination of knowledge throughout an organization.
• Work faster, reuse best practices, and reduce costly rework from project to project.Thank you.. -

Objective of Business Warung Internet
Client: Personal
• Memberikan paparan yang jelas tentang dana yang dibutuhkan.
• Memberikan detail spesifikasi hardware dan software.
• Memastikan bahwa anggaran yang digunakan bisa digunakan secara optimal sehingga tidak ada resiko diluar dugaan yang akan timbul.
• Membantu dan memastikan pembangunan usaha dapat dilaksanakan dengan baik.Thank you.. -

Objective of Security Development Lifecycle
Client: Public + Private Company and Government
• Significantly reduce threat, vulnerability and risk from software.
• Help address compliance requirement, proactive security.
• Improve productivity and efficiency application development.
• Reduce cost and make better return of investment.
• Better product with less bugs and vulnerability.Thank you.. -
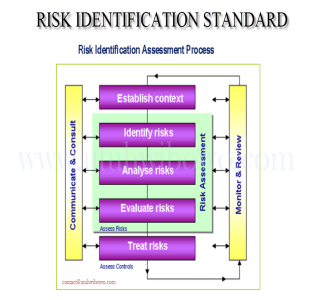
Risk Identification Standard Process
Client: All Sector
• Implementation risk management standard.
• Identification key and evaluate risk.
• Provide risk matrix and scoring.
• Mapping and analyze risk impact.
• Monitoring and maintain risk.
• Communicate and close risk.
• Manage risk control self assessment.Thank you.. -
Kemampuan Dalam Memimpin: Cara Berbeda dan Bernilai Lebih
-
Teknik-Teknik Negoisasi Yang Efektif Dan Efisien
-
Peningkatan Keamanan Situs Web Pemerintah Indonesia
-
Attack Vector Dalam Ranah Information Security
-
Optimalisasi Database: Meningkatkan Performance dan Utilitas
-
SEO: Search Engine Optimization
-
Belajar Gratis Membuat Website Dengan Content Management System
-
Wajib! Lindungi Email Pribadi Anda
-
Administrasi Linux Virtual Private Server
-
Rahasia Membangun Website Cantik dan Menarik
















